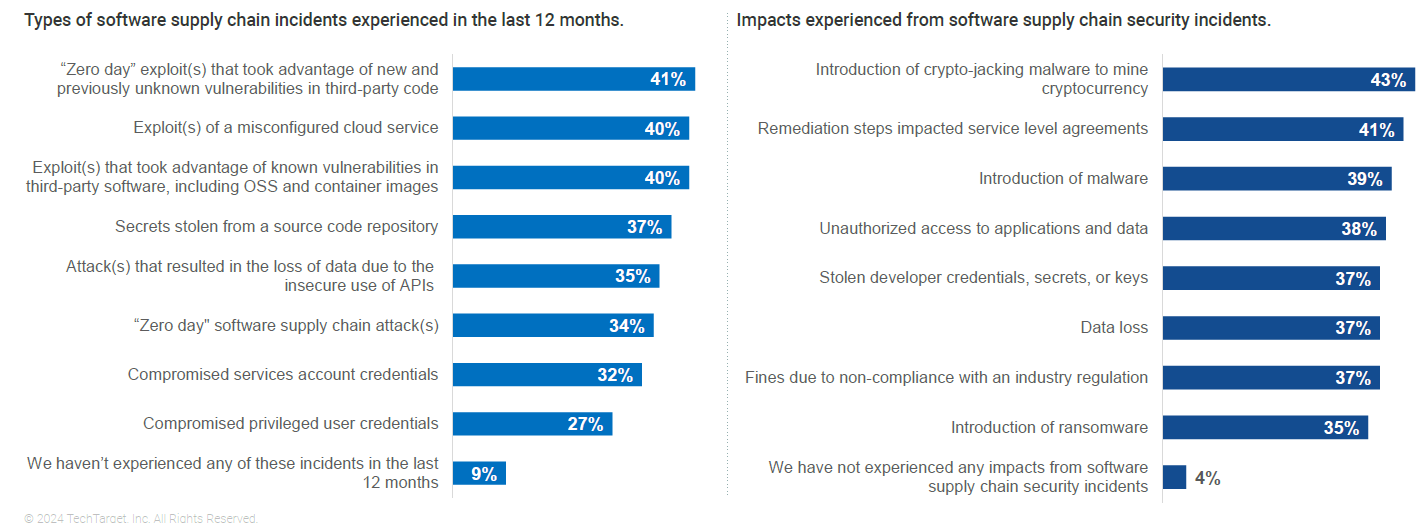
A stunned 91% Enterprises have suffered software supply chain incidents in just one year, underscoring the need for better security for continuous integration/continuous deployment (CI/CD) pipelines.
Four in 10 enterprises say that misconfigured cloud services, secrets stolen from source code repositories, insecure use of APIs and compromised user credentials are becoming commonplace. The most common effects of these attacks are malicious introduction of crypto-jacking malware (43%) and required remediation measures affecting SLAs (service level agreements) (41%).
Of those enterprises that experienced software supply chain incidents in the past 12 months, 96% had some impact. Source: The Growing Complexity of Securing the Software Supply Chain, Enterprise Strategy Group
Attackers are using AI to fine-tune their tradecraft and launch attacks that overwhelm any organization’s ability to keep up. With offensive AI being used by attackers to their advantage, cyber security vendors need to rise to the challenge and advance on AI to gain a broad defense advantage and not lose the AI war.
VB event
AI Impact Tour – NYC
We’ll be in New York on February 29 in partnership with Microsoft to discuss how to balance the risks and rewards of AI applications. Request an invitation to a special event below.
Request an invitation
Why software supply chains are a high value target
Attacking the software supply chain is the ransom multiplier every attacker is looking for. Nation-state attackers, cybercrime syndicates, and advanced persistent threat (APT) groups routinely target software supply chains because they are historically the least-protected sector of any software company or business. Examples include the Okta breach, the JetBrains supply chain attack, MOVEit, 3CX, Applied Materials, PyTorch Framework, Fantasy Viper, and the Kaseya VSA ransomware attack. In these incidents, attackers exploited vulnerabilities in the software supply chain, affecting hundreds of businesses around the world.
Five areas where AI is strengthening supply chain security
Keeping pace in the AI arms race is becoming increasingly challenging. That’s especially true if you’re an organization fighting adversaries using the latest generative AI tools, including FraudGPT and other AI tools. The good news is that AI is showing signs of intrusions and breaches being recognized and slowing down – but not stopping entirely – with the CI/CD pipeline in mind. Five areas where AI is having an impact include:
CNAPP relies on AI to automate hybrid and multicloud security while shifting security remaining in the SDLC. Cloud-native application protection platforms (CNAPPs) that have AI and machine learning (ML) integrated into their platform are effective in helping DevSecOps identify threats early when code is written into applications before they are scanned into GitHub and other repositories. . CNAPP integrates various security capabilities, including Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP) with other tools such as entitlement management, API controls and Kubernetes posture control, to provide comprehensive security for all cloud-native applications. . their entire life cycle. Leading CNAPP vendors include Cisco, CrowdStrike, Juniper Networks, Sophos, Trend Micro, Zscaler and others.

CNAPP integrates a variety of security applications into a single, unified platform to improve data visibility and predictive accuracy, all contributing to robust cloud security posture management. Source: Gartner, How Cloud-Agnostic Tools Can Secure Your Multicloud, February 5, 2024
AI continues to harden endpoint security down to the identity level while defining the future by training LLMs. Attackers can use AI to discover many forms of privileged access credentials to get into an endpoint, then use those credentials to attack other endpoints and move across the network. Closing the gap between identity and endpoints is a great use case for AI.
Parallel development among leading extended detection and response (XDR) providers is also gaining momentum. Crowdstrike “One of the areas we’ve really pioneered is that we can take weak signals from different endpoints,” co-founder and CEO George Kurtz told a keynote audience at the company’s annual Fal.Con event last year. And we can link these together to find novel inventions. We are now extending this to our third-party partners so that we can look at other weak signals across domains and come up with new discoveries, not just at endpoints.”
Leading XDR platform providers include Broadcom, Cisco, CrowdStrike, Fortinet, Microsoft, Palo Alto Networks, SentinelOne, Sophos, TEHTRIS, Trend Micro and VMWare. Augmenting LLM with telemetry and human-annotated data defines the future of endpoint security.
Adaptive Automated Threat Detection: AI/ML models are designed to continuously learn from behavior and data patterns and, over time, derive more adaptive automated threat detections. XDR and CNAPP vendors are using endpoint data to train their LLMs to further improve how adaptable they are to automated threat detection and detection.
Given the strong push by DevSecOps teams to gain greater visibility across the CI/CD pipeline, automated threat detection is increasingly being delivered as part of the CNAPP platform. Identifying and ranking vulnerabilities and risks is a big part of DevSecOp’s role today, creating AI-based automated risk detection that can adapt to real-time table stacks to protect CI/CD pipelines.
AI is streamlining and simplifying analytics and reporting across the CI/CD pipeline, identifying potential threats or bottlenecks early and predicting attack patterns. One of the reasons XDR and CNAPP vendors are doubling down on training their large language models (LLM) with endpoint and attack data is to sharpen the accuracy of risk prioritization and context analysis. CNAPP relies on a unified data lake and graph database for event logging, reporting, alerting, and relationship mapping, making it an ideal data set for training LLM and long-running ML algorithms. AI-enhanced analytics ensure that the most critical threats are addressed first, protecting the integrity of the software supply chain.
Using AI and ML to automate patch management. Automated patch management while capitalizing on diverse datasets and integrating them into a risk-based vulnerability management (RBVM) platform is a perfect use case for AI. Leading AI-based patch management systems can interpret vulnerability assessment telemetry and prioritize threats by patch type, system and endpoint. Leading vendors include Atera, Automox, BMC Client Management Patch Powered by Ivanti, Canonical, ConnectWise, Ivanti, Jamf, Kaseya, Sysword, SixSense, Tanium, and others.
“Patching is not nearly as easy as it sounds,” said Srinivas Mukamala, Ivanti’s chief product officer. “Well-staffed, well-funded IT and security teams experience priority challenges even in the midst of other pressing demands. To reduce risk without increasing workload, organizations should implement a risk-based patch management solution and leverage automation to identify, prioritize and address vulnerabilities without excessive manual intervention.”
VentureBeat’s Mission Digital Town is to become a square for technology decision makers to gain knowledge about transformative enterprise technologies and transactions. Find our briefings.
#ways #helping #DevOps #teams #mitigate #supply #chain #attacks




Leave a Reply